There are some surprising numbers available that tell a dark story about mobile apps and what they can be doing on your device.
By now you've read about malicious apps that leak privacy data, but do you realize how serious it really is? If not, you'd better pay attention to the following statistics gathered by Symantec*. And if you think that Google Play is 100% safe, it isn't. I have some data that yields some shocking results about the number of malicious apps waiting to grab your data.
===> Unfortunately, the playing surface for Internet naughtiness has changed in the past couple of years and you need to know that it's only getting worse. <===



 Your new post is loading...
Your new post is loading...


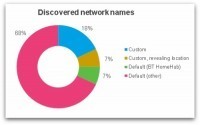

![Why You Should Care About Mobile Security [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)




===> Unfortunately, the playing surface for Internet naughtiness has changed in the past couple of years and you need to know that it's only getting worse. <===
Check also:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
Oh dear - the world of technology seems to be one step forward two steps back but these issues are important especially of we are going to be using mobile devices in education and promoting BYOD approaches.