The game of cat-and-mouse between malware authors and security white hats may have entered a new phase this week, thanks to an aggressive new malware system that doesn’t just attempt to obfuscate its own operation — it aggressively scans for clues that others are monitoring its actions. If it detects that it’s operating within a Virtual Machine, the malware, dubbed Rombertik, will go nuclear and attempt to overwrite the master boot record of the local hard drive.
Cisco’s threat response team has detailed the operation of Rombertik, and the malware’s obfuscation and attack vectors are unique. Once installed, it’s a fairly standard data sniffer that grabs indiscriminately from the information available on an infected PC. What sets Rombertik apart is the way it checks to see if it’s running in a VM-provided sandbox, and the actions it takes if it finds itself in such a mode.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Rombertik



 Your new post is loading...
Your new post is loading...

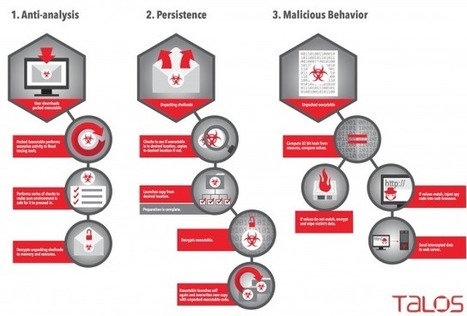





The game of cat-and-mouse between malware authors and security white hats may have entered a new phase this week, thanks to an aggressive new malware system that doesn’t just attempt to obfuscate its own operation — it aggressively scans for clues that others are monitoring its actions. If it detects that it’s operating within a Virtual Machine, the malware, dubbed Rombertik, will go nuclear and attempt to overwrite the master boot record of the local hard drive.
Cisco’s threat response team has detailed the operation of Rombertik, and the malware’s obfuscation and attack vectors are unique. Once installed, it’s a fairly standard data sniffer that grabs indiscriminately from the information available on an infected PC. What sets Rombertik apart is the way it checks to see if it’s running in a VM-provided sandbox, and the actions it takes if it finds itself in such a mode.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Rombertik