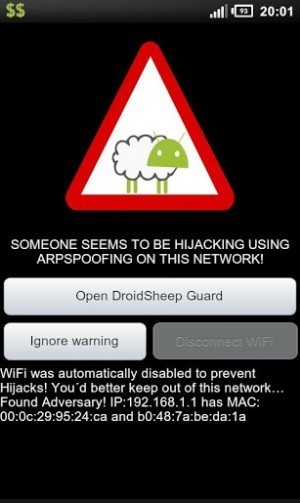
DroidSheep Guard protects your phone from DroidSheep, Faceniff & other hijackers DroidSheep Guard protects your phone from Tools like DroidSheep, Faceniff and other Se...
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
21st Century Tools to help teaching-people and learners to achieve "BETTER" their tasks...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|
|







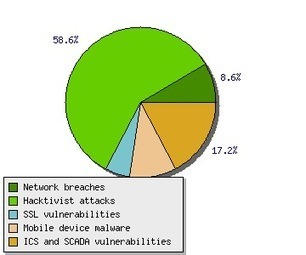



Awareness and Protection!!!