Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
August 16, 2013 8:37 AM
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free

Gust MEES's curator insight,
August 16, 2013 8:40 AM
===> making sure that the Android system setting ‘Unknown sources’ is unchecked to prevent dropped or drive-by-download app installs and installing security apps like Lookout to as their first line of defense against malware. <===
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free

Gust MEES's curator insight,
July 22, 2013 2:48 PM
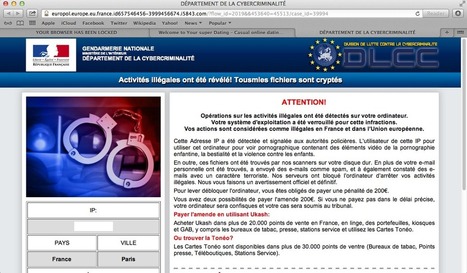
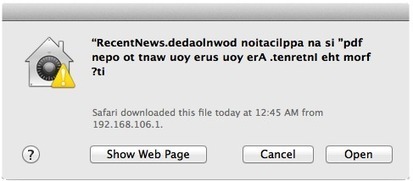
Further customizations of the Mac ransom pages discovered today shows the bad guys are busy updating their templates for each country's police force.
===> Not all countries currently have their own ‘theme’ but it is only a matter of time before the bad guys roll them out. <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=RANSOMWARE

Gust MEES's curator insight,
July 22, 2013 2:53 PM
Further customizations of the Mac ransom pages discovered today shows the bad guys are busy updating their templates for each country's police force.
===> Not all countries currently have their own ‘theme’ but it is only a matter of time before the bad guys roll them out. <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=RANSOMWARE

Gust MEES's curator insight,
July 22, 2013 3:03 PM
Further customizations of the Mac ransom pages discovered today shows the bad guys are busy updating their templates for each country's police force.
===> Not all countries currently have their own ‘theme’ but it is only a matter of time before the bad guys roll them out. <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=RANSOMWARE

Gust MEES's curator insight,
July 17, 2013 6:06 PM
Tumblr has released a "very important" update for their iPad and iPhone apps following what they describe as a "security lapse".
It appears that passwords were being sent over the internet unencrypted, making it easy for anyone with bad intentions and a little technical knowledge to harvest Tumblr users' login details.
Learn more:
- https://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Passwords

midnight's curator insight,
April 7, 2014 5:54 AM
This article contains information about the security of the iphone and ipad users. This is very useful, because users wil be secured from any harm that could be done with their gadets. passwords were being sent over the internet unencrypted this could cause alot of problems because hackers would easily be able to access your password.

Gust MEES's curator insight,
July 12, 2013 1:31 AM
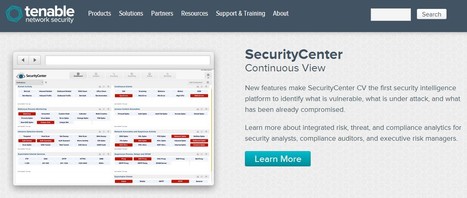
New features make SecurityCenter CV the first security intelligence platform to identify what is vulnerable, what is under attack, and what has been already compromised.

Gust MEES's curator insight,
July 7, 2013 5:01 AM
Why You Need Mac Antivirus Software. Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Gust MEES's curator insight,
July 7, 2013 5:04 AM
Why You Need Mac Antivirus Software. Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|

Gust MEES's curator insight,
September 11, 2013 10:31 AM
Users of Adobe Reader or Acrobat XI for Windows and Mac OS X are advised to upgrade to Adobe Reader XI (11.0.04) or Adobe Acrobat XI (11.0.04), respectively. Adobe Reader and Acrobat X for Windows and Mac have also been updated to version 10.1.8. 
Terheck's curator insight,
September 11, 2013 10:50 AM
Links for downloads : Flash player : https://www.adobe.com/products/flashplayer/distribution3.html Shockwave player : http://get.adobe.com/fr/shockwave/ Adobe AIR : http://get.adobe.com/fr/air/

Gust MEES's curator insight,
August 23, 2013 1:14 PM
Learn more with Infographics:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic

Gust MEES's curator insight,
August 23, 2013 1:19 PM
Learn more with Infographics:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic

Gust MEES's curator insight,
August 14, 2013 5:19 PM
Joomla vulnerabilities have been a particular problem; 57 percent of the attacks Versafe has seen this year have come from sites hosted on the platform, up from 41 percent last year.
Learn more:
- http://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Joomla

Gust MEES's curator insight,
August 14, 2013 5:22 PM
Joomla vulnerabilities have been a particular problem; 57 percent of the attacks Versafe has seen this year have come from sites hosted on the platform, up from 41 percent last year.
Learn more:
- http://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Joomla

Gust MEES's curator insight,
August 6, 2013 9:16 AM
BGP Ranking is used by CIRCL (Computer Incident Response Center Luxembourg):

Gust MEES's curator insight,
August 1, 2013 10:15 AM
Learn more:
- http://www.scoop.it/t/ict-security-tools

Gust MEES's curator insight,
August 1, 2013 10:16 AM
Learn more:
- http://www.scoop.it/t/ict-security-tools

Gust MEES's curator insight,
August 1, 2013 10:22 AM
Learn more:
- http://www.scoop.it/t/ict-security-tools

Gust MEES's curator insight,
July 30, 2013 4:45 PM
===> Think you're safe because you use OS X or Linux? Think again! There are devices being marketed that claim to be able to get infiltrate these operating systems too. <===
Nobody Is Perfect!!!

Gust MEES's curator insight,
July 30, 2013 4:48 PM
===> Think you're safe because you use OS X or Linux? Think again! There are devices being marketed that claim to be able to get infiltrate these operating systems too. <===
Nobody Is Perfect!!!

Gust MEES's curator insight,
July 21, 2013 8:20 PM
===> We hear a lot about mobile apps and devices being hacked, however as I have stated before that is small potatoes when compared to the treasure trove of the back-end systems that power mobile applications and services. <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Gust MEES's curator insight,
July 21, 2013 8:22 PM
===> We hear a lot about mobile apps and devices being hacked, however as I have stated before that is small potatoes when compared to the treasure trove of the back-end systems that power mobile applications and services. <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Vivalist's curator insight,
July 22, 2013 4:28 AM
going up the network, identify the bottle neck and get at it - pretty simple, but they probably had to sweat a little to do it.

Gust MEES's curator insight,
July 18, 2013 5:33 PM
Watch log files for command instances, such as file creation and modification. However, the key point is to stay on top of updates, especially for platforms such as WordPress and Joomla, which are popular targets for attackers and constantly updated in order to address security concerns.
Learn more:
- http://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/

Gust MEES's curator insight,
July 18, 2013 5:37 PM
Watch log files for command instances, such as file creation and modification. However, the key point is to stay on top of updates, especially for platforms such as WordPress and Joomla, which are popular targets for attackers and constantly updated in order to address security concerns.
Learn more:
- http://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/

Gust MEES's curator insight,
July 16, 2013 6:00 PM
===> Bill Mellon of the University of Wisconsin said the school has seen as many as 100,000 hacking attempts a day from China. <=== AND YOU THINK that there isn't STILL a MUST for Learning and Teaching about Cyber-Security, seriously!!!???
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Universities
- http://www.scoop.it/t/securite-pc-et-internet/?tag=DATA-BREACHES

Jhonathan Garcia's curator insight,
July 10, 2013 9:33 PM
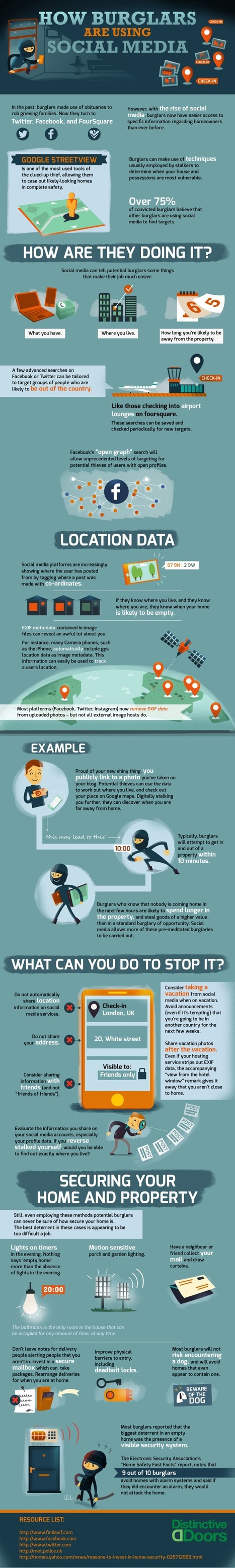
Social Media Security Post: Be careful with all the things you post! 
Michelle Gilstrap's curator insight,
July 11, 2013 1:13 PM
Never show photos of your vacation while you are on vacation. Always show photos when you get back home. 
Carmenne Kalyaniwala's curator insight,
October 15, 2013 2:36 AM
An infographic with some important information we can share with students |


























Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security